1. TOOLS AND ENV
IDE : Spring Tool Suite 3.7.3
JDK : 1.8 Tomcat : 8.0.18
Spring : 4.2.6.RELEASE
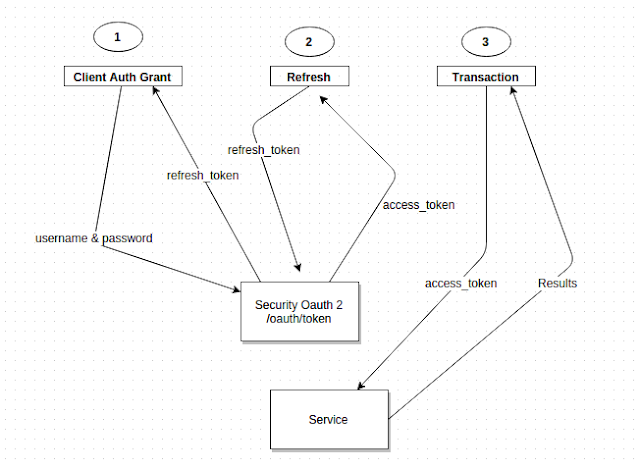
2. OAUTH2 FLOW
Basically , resources are protected with access token, client could use refresh token to request an access token if authenticated with its credentials.
3. POM.XML
spring-security-oauth2 added to the dependency.
4. OAUTH2 CONFIG
1. Technically authorization server and resource server can be hosted separately.
2. OAuth2 authentication manager is define in Spring Web Security in class SecurityConfig
3. You may refer to Spring documents for all possible values and use cases for grant types and scopes
5. JS AND JSP
1. Get OAUTH2 token before consuming api restful web service
2. csrf is disabled just to make example simple
6. TEST
7. SOURCE CODE
https://github.com/junjun-dachi/spring-tutorials/tree/master/05-spring-mvc-oauth2
8. Reference
https://spring.io/guides/tutorials/spring-boot-oauth2/
https://github.com/spring-projects/spring-security-oauth
https://github.com/spring-projects/spring-security-oauth/blob/master/docs/oauth2.md
https://raymondhlee.wordpress.com/2014/12/21/implementing-oauth2-with-spring-security/


Anyone can take the 5-minute java test in the US as it is targeted to coders who want to test their Java knowledge.
ReplyDelete